
Business Cyber Security General Knowledge
The purpose of a cybersecurity report is to provide an organization with a comprehensive overview of its cybersecurity posture, identify potential vulnerabilities and threats, and provide recommendations for improving its cybersecurity posture.
A cybersecurity report serves several purposes, including:
- Providing an overview of the organization’s cybersecurity posture: A cybersecurity report provides an in-depth analysis of an organization’s cybersecurity systems, policies, and practices, giving decision-makers a clear understanding of the organization’s cybersecurity strengths and weaknesses.
- Identifying potential vulnerabilities and threats: A cybersecurity report identifies potential vulnerabilities and threats that could impact the organization’s operations, reputation, and financial stability. This information is critical for decision-makers to develop effective risk management strategies and implement appropriate cybersecurity measures.
- Assessing risk exposure: A cybersecurity report analyzes an organization’s risk exposure, including the potential impact of a cyber attack on the organization. This information is critical for decision-makers to allocate resources appropriately and prioritize cybersecurity initiatives.
- Providing actionable recommendations: A cybersecurity report provides recommendations for improving the organization’s cybersecurity posture, including steps to address vulnerabilities and reduce risk exposure. These recommendations provide decision-makers with a roadmap for improving the organization’s cybersecurity posture and reducing the risk of cyber attacks.
Overall, the purpose of a cybersecurity report is to provide an organization with a comprehensive understanding of its cybersecurity posture, identify potential vulnerabilities and threats, and provide actionable recommendations for improving its cybersecurity posture.
Get in touch today to book your free initial consultation. We can provide you with a professional cyber security report making your organization less vulnerable to attack!
Contact us here now!

Business Cyber Security General Knowledge
A cybersecurity report is a document that provides an overview of an organization’s cybersecurity posture, including its strengths and weaknesses, and recommendations for improvements. Cybersecurity reports are typically generated by cybersecurity professionals or third-party consultants, who conduct a thorough analysis of an organization’s cybersecurity systems, processes, and policies.
A cybersecurity report typically includes the following information:
- Executive Summary: A brief summary of the report’s findings, including the organization’s current cybersecurity posture and key areas for improvement.
- Overview of Cybersecurity Systems: A detailed overview of the organization’s current cybersecurity systems, including firewalls, intrusion detection systems, anti-virus software, and other security tools.
- Threat Assessment: An analysis of the potential cyber threats that the organization may face, such as malware, phishing attacks, or social engineering.
- Vulnerability Assessment: An assessment of the organization’s vulnerabilities, including weaknesses in its cybersecurity systems, policies, and practices.
- Risk Analysis: An analysis of the organization’s risk exposure, including the potential impact of cyber attacks on the organization’s business operations, reputation, and financial stability.
- Recommendations: A list of recommendations for improving the organization’s cybersecurity posture, including steps to address vulnerabilities and reduce risk exposure.
Overall, a cybersecurity report is a valuable tool for organizations that want to improve their cybersecurity posture and reduce the risk of cyber attacks. It provides a comprehensive assessment of an organization’s cybersecurity systems, identifies areas for improvement, and provides actionable recommendations to enhance the organization’s cybersecurity posture.
Get in touch today to book your free initial consultation. We can provide you with a professional cyber security report making your organization less vulnerable to attack!
Contact us here now!

Business Cyber Security General Knowledge
IT remote support technicians require a combination of technical and soft skills to be successful in their role. Here are some of the essential skills that IT remote support technicians should possess:
- Technical Knowledge: IT remote support technicians must have a strong understanding of computer hardware, software, and networking concepts, as well as experience with remote desktop support tools and troubleshooting techniques.
- Communication Skills: IT remote support technicians should have excellent communication skills, both verbal and written, to effectively communicate technical information to users with varying levels of technical knowledge.
- Problem-Solving Skills: IT remote support technicians must be able to quickly and effectively diagnose technical issues, identify the root cause, and provide effective solutions to resolve the problem.
- Customer Service: IT remote support technicians must have a customer-centric mindset, ensuring that users are satisfied with the support they receive and their issues are resolved in a timely and efficient manner.
- Adaptability: IT remote support technicians must be adaptable and able to work in a fast-paced, ever-changing environment, as they may be required to work with different technologies and support different types of users.
- Attention to Detail: IT remote support technicians should have a keen eye for detail, ensuring that technical issues are accurately diagnosed and resolved to prevent future problems.
- Time Management: IT remote support technicians must be able to manage their time effectively, balancing multiple support requests and prioritizing tasks based on their urgency and impact on users.
Overall, IT remote support technicians must have a combination of technical and soft skills to be successful in their role. They must be able to work independently and as part of a team, effectively communicate technical information, and provide high-quality technical support to users.
Get in touch today to book your free initial consultation. We can provide remote IT system support making your organization less vulnerable to attack!
Contact us here now!

Business Cyber Security General Knowledge
The general duties of remote IT support technicians include providing technical assistance and resolving technical issues for users and organizations from a remote location. Here are some of the common duties of remote IT support:
- Troubleshooting: Remote IT support technicians are responsible for identifying and resolving technical issues that users encounter, such as software errors, hardware failures, connectivity issues, and other IT-related problems.
- Technical Support: Remote IT support technicians provide technical support to users and organizations, answering questions, providing guidance, and helping users troubleshoot issues they may encounter.
- Maintenance and Updates: Remote IT support technicians may be responsible for maintaining IT systems and ensuring that they are up-to-date with the latest security patches and software updates.
- Remote Desktop Support: Remote IT support technicians can remotely connect to users’ computers and IT systems, allowing them to provide assistance and resolve issues as if they were physically present.
- Documentation and Reporting: Remote IT support technicians are responsible for documenting their work and providing reports on the issues they resolve, the solutions they provide, and the overall status of IT systems.
- Customer Service: Remote IT support technicians must have strong customer service skills, providing a high level of customer service to users and ensuring that their technical issues are resolved in a timely and efficient manner.
Overall, the duties of remote IT support technicians may vary depending on the specific organization and the nature of the IT systems they support. However, they are generally responsible for providing technical support and resolving technical issues remotely, ensuring that IT systems are functioning optimally and users are satisfied with the level of support they receive.
Get in touch today to book your free initial consultation. We can harden your IT systems making your organization less vulnerable to attack!
Contact us here now!

Business Cyber Security General Knowledge
Remote IT support refers to the process of providing technical support and troubleshooting services to users and organizations from a remote location. Instead of an IT technician being physically present on-site, they can connect to the user’s computer or IT system over the internet or a network and provide assistance remotely.
Remote IT support can be delivered in several ways, such as email, phone, chat, or remote desktop access. With remote desktop access, the IT technician can view and control the user’s computer, which allows them to diagnose and fix technical issues as if they were physically present on-site.
Remote IT support is becoming increasingly popular, especially with the rise of remote work and the need for IT support in different locations. Remote IT support allows for quicker response times and faster problem resolution since technicians can provide support from anywhere, without needing to travel to the location. It can also reduce costs since it eliminates the need for on-site IT staff.
Overall, remote IT support is a convenient and efficient way for organizations and individuals to receive technical support and resolve IT issues, regardless of their location.
Get in touch today to book your free initial consultation. We can provide affordable remote IT system support making your organization less vulnerable to attack!
Contact us here now!

Business Cyber Security General Knowledge
The process of IT system hardening involves a series of steps that are designed to make a system more secure and less vulnerable to cyber attacks and other security threats. Here is an overview of the typical process of IT system hardening:
- Identify and Assess Risks: The first step in the process is to identify potential security risks and vulnerabilities in the system. This may involve performing a security audit, vulnerability assessment, or penetration testing. By identifying risks and vulnerabilities, you can prioritize the hardening measures that are needed to protect the system.
- Configure the System: The next step is to configure the system to reduce the attack surface and limit potential vulnerabilities. This may include disabling unnecessary services and protocols, removing default accounts and passwords, and implementing access controls.
- Apply Security Updates: The system should be kept up-to-date with the latest security updates, patches, and fixes to address any known security vulnerabilities.
- Implement Security Controls: Security controls, such as firewalls, intrusion detection and prevention systems, and anti-virus software should be implemented to protect the system and monitor for security threats.
- Test the System: The hardening measures should be tested to ensure that they are effective and do not impact system performance. This may involve testing for security vulnerabilities, performing penetration testing, and monitoring for security threats.
- Monitor and Maintain: Finally, the system should be continuously monitored and maintained to ensure that it remains secure over time. This includes monitoring for security threats, applying updates and patches, and performing regular security assessments.
Overall, the process of IT system hardening is an ongoing effort that requires regular attention and updates to ensure that the system remains secure over time.
Get in touch today to book your free initial consultation. We can harden your IT systems making your organization less vulnerable to attack!
Contact us here now!

Business Cyber Security General Knowledge
The process of hardening an IT system typically involves multiple steps, but here are three of the main steps to consider:
- Identify Security Risks: The first step in hardening an IT system is to identify security risks and vulnerabilities. This may involve performing a security audit, vulnerability assessment, or penetration testing. By identifying security risks, you can develop a plan to mitigate those risks and improve the overall security posture of your IT system.
- Implement Security Controls: The next step is to implement security controls that address the identified risks and vulnerabilities. This may include configuring firewalls, implementing access controls, disabling unnecessary services and protocols, and applying security patches and updates. It is important to ensure that these controls are appropriate for the system and environment in question, and that they are implemented in accordance with best practices.
- Monitor and Update: The final step in hardening an IT system is to continuously monitor and update the system. This includes monitoring for security threats, vulnerabilities, and breaches, and applying updates and patches as needed. Regular security assessments and testing can help to identify new risks and vulnerabilities, and ensure that your system remains secure over time.
Overall, hardening an IT system is an ongoing process that requires regular attention and updates. By following these main steps, you can help to ensure the security and integrity of your IT assets.
Get in touch today to book your free initial consultation. We can harden your IT systems making your organization less vulnerable to attack!
Contact us here now!

azure, compliance, IT Cyber Security Technical Knowledge, m365, microsoft, o365
Microsoft recently turned on security defaults for M365 Tenants forcing MFA for users.
You can check by going into Azure AD > Properties > Manage Security defaults
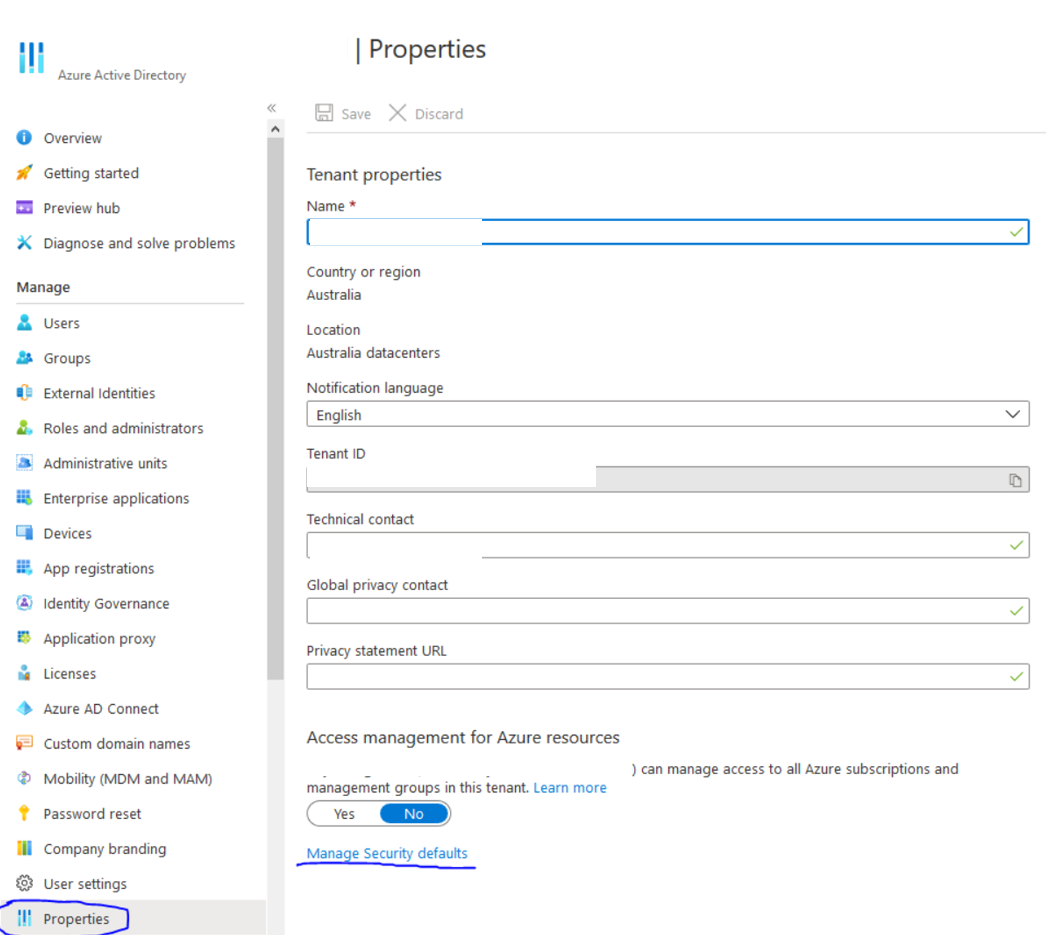
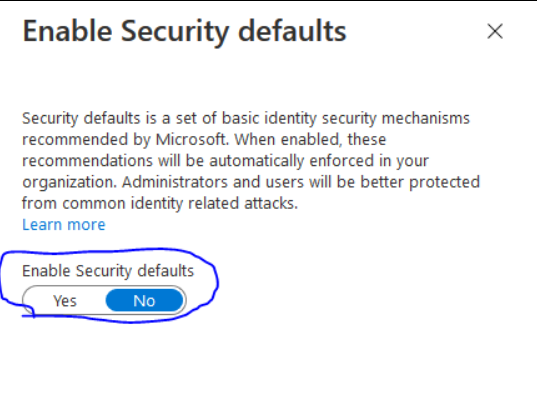
If defaults are set to “Yes” that is the reason MFA turned on. You should be able to set that to NO to remove the “new” defaults and turn MFA off. – However it is highly recommended to use MFA for all accounts.

active directory, Exchange, microsoft, Windows Server
Sometimes when performing exchange server updates after rebooting the server it will hang on ‘Getting Windows Ready’ then sometimes when logging in it may lock up again and become unresponsive.
This is a common issue with Exchange 2013 and Windows Server 2012 R2 Operating System.
Follow the guide below to resolve this issue.
I restarted VM few times, but the Exchange Server VM was unusable.
The best solution is to enter Boot Menu and run VM in Safe Mode.
For this we have to boot VM from Windows Server 2012 R2 ISO and instead of Install option, we select Repair your computer.
After selecting Troubleshoot, we enter Command Prompt.
We enable Boot Menu on our Windows Server 2012 R2 OS of Exchange Server VM by entering commands:
bcdedit /set {bootmgr} displaybootmenu yes
bcdedit /set {bootmgr} timeout 15
After VM reboot, we can enter Boot Menu by pressing F8 and select Safe Mode option.

In Safe Mode Exchange Server VM starts without problems.
Go into Services and disable all Exchange Services on VM (by changing Start-up Type of services to Manual). After this reboot the VM in normal way and machine will start.
Re-enable Exchange Services again (by changing Start-up Type of services to Automatic) and reboot VM.
The Exchange Server should now boot up straight away without being stuck at the ‘Getting Windows Ready’ screen

active directory, compliance, gpo, group policy, IT Cyber Security Technical Knowledge, microsoft, networking, ransomware, Windows Server
Create Group Policy to Whitelist Applications – Ransomware prevention
Recommended to test Whitelisting in a test environment before deploying in production environment. Purpose is to Block Ransomware, Block Java Updates You will need to manually add Whitelist entries for each new Java Update you wish to install
Go to https://java.com/en/download/
Take note of the latest Java Version (eg, 8u301)
Login to your to a server that can Access/Create/Edit Group Policy objects
Open the run command, type in gpmc.msc – Click OK
Right click on the Organizational Unit you wish add the Whitelist to, Select the first option.
(Create GPO)
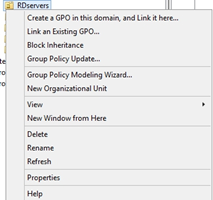
Enter a name for the Whitelist, Click OK (i.e CryptoLocker/Ransomware Prevention)
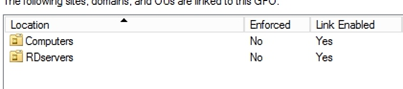
Link the newly create GPO to any other Organizational Units you want to be added to the GPO.
(eg. Right click on Computers OU, ‘select Link an Existing GPO…’ then select the new GPO)
Right click on the GPO, click Edit…
Drill down in; Computer Configuration >> Policies >> Windows Settings >> Security Settings >> Software Restriction Policies
Right click on Software Restriction Policies, Select the first option

Right click on Additional Rules, Select New Path Rule…
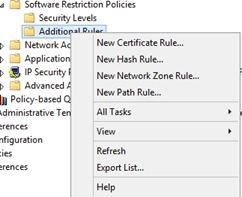
Enter the following path: %localAppData%\*\*.exe
Security Level = Disallowed
Click OK

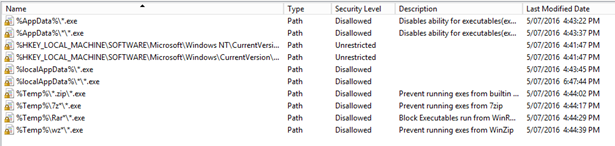
Create Additional Path Rules for the following paths:
%localAppData%\*.exe
%AppData%\*.exe
%AppData%\*\*.exe
%Temp%\*.zip\*.exe
%Temp%\7z*\*.exe
%Temp%\Rar*\*.exe
%Temp%\wz*\*.exe
Your list should look like this:
Exit out of Group Policy Editor.
Create another GPO called Cryptolocker/Ransomware – Whitelist Allow (Link to same OU’s as previous GPO)
Right click on the GPO, click Edit…
Drill down in; – Computer Configuration >> Policies >> Windows Settings >> Security Settings >> Software Restriction Policies
Right click on Software Restriction Policies, Select the first option

Right click on Additional Rules, Select New Path Rule…

Under ‘Path:’ enter the path of the Java Installer you wish to allow:
%localappData%\temp\jre-8u301-windows-i586-iftw.exe
Depending on which version of Java you are updating, replace ‘8u91’ with the version you want to allow.
Set Security Level to ‘Unrestricted’
Enter an appropriate description name.
Click OK.

Verify that new Path Rule has been added to Whitelist.
Close GPO Editor.
Refresh Group policy Management
Go down to the Whitelisting Çryptolocker/Ransomware – Whitelist Allow GPO, click on it once
In the window on the right select ‘Settings’ from the tabs.
Drill down to; Computer Configuration >> Policies >> Windows Settings >> Security Settings >> Software Restriction Policies/Additional Rules
Verify that new Path rule is shown in Policy List.
Exit Group Policy Management.
Go to a machine what is linked to the GPO to test whitelist.
Run Java Updater/Installer
Note the successful installation of Java
If fails = Perform forced Update to GPO
From Administrative Command Prompt,
gpupdate /force























