
microsoft, networking, windows 10, windows 11
Bypass Windows 11 Network Setup to create a local user account.
Whether you are turning on your new device for the first time or performed a clean installation of Windows 11, say are always prompted to join a WiFi Network if you are not using an Ethernet cable to connect to the internet, follow the steps below to bypass this network setup so you can create a local account without needing a Microsoft account.
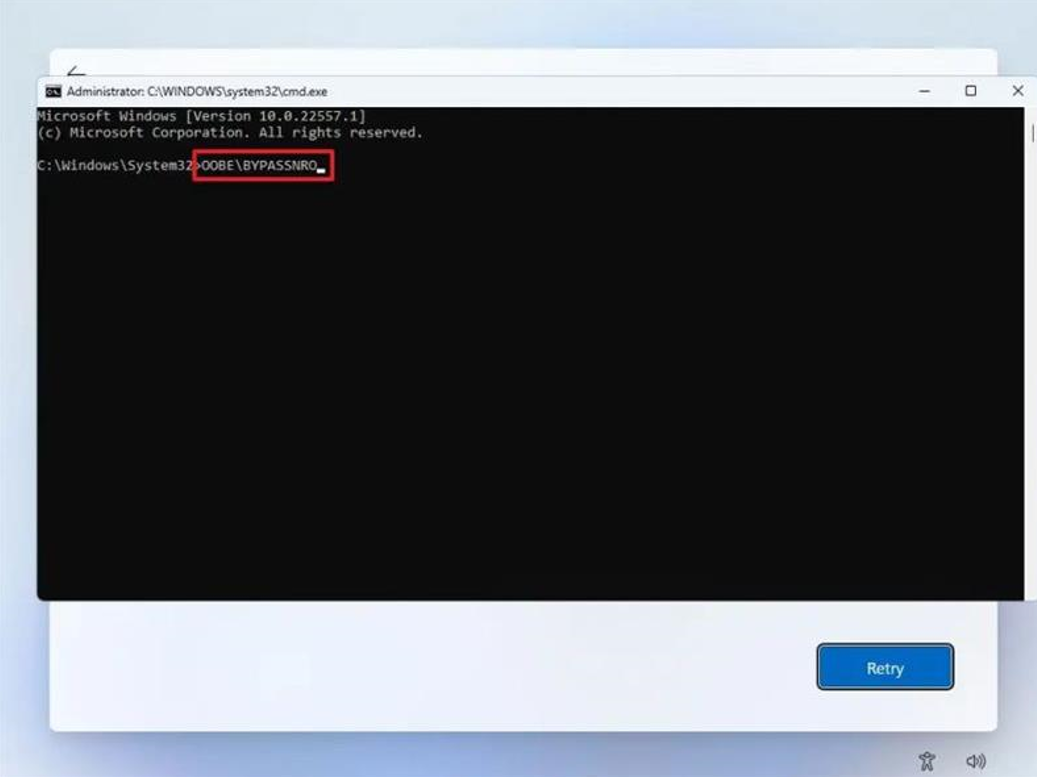
On the “Let’s connect you to a network” page, use the Shift + F10 keyboard shortcut.
In Command Prompt, type the OOBE\BYPASSNRO command to bypass network requirements on Windows 11 and press Enter.
The computer will restart automatically, and the out-of-box experience (OOBE) will start again.
Quick note: You will need to select the region and keyboard settings one more time to get to the network connection page.
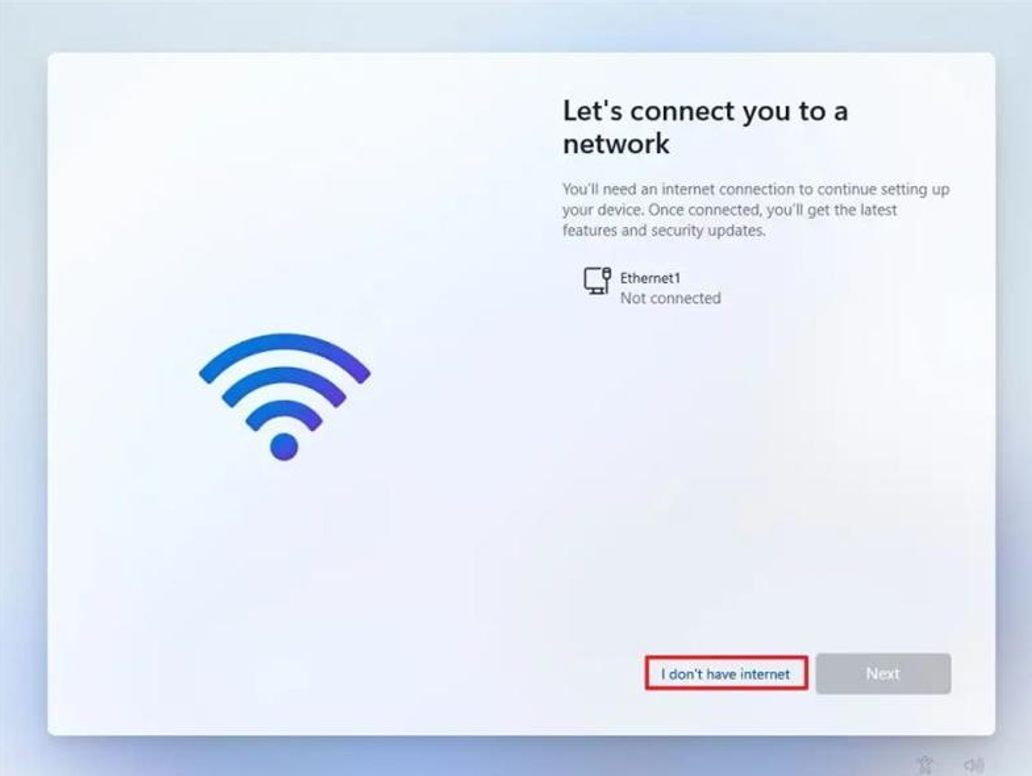
Click the “I don’t have internet” option.
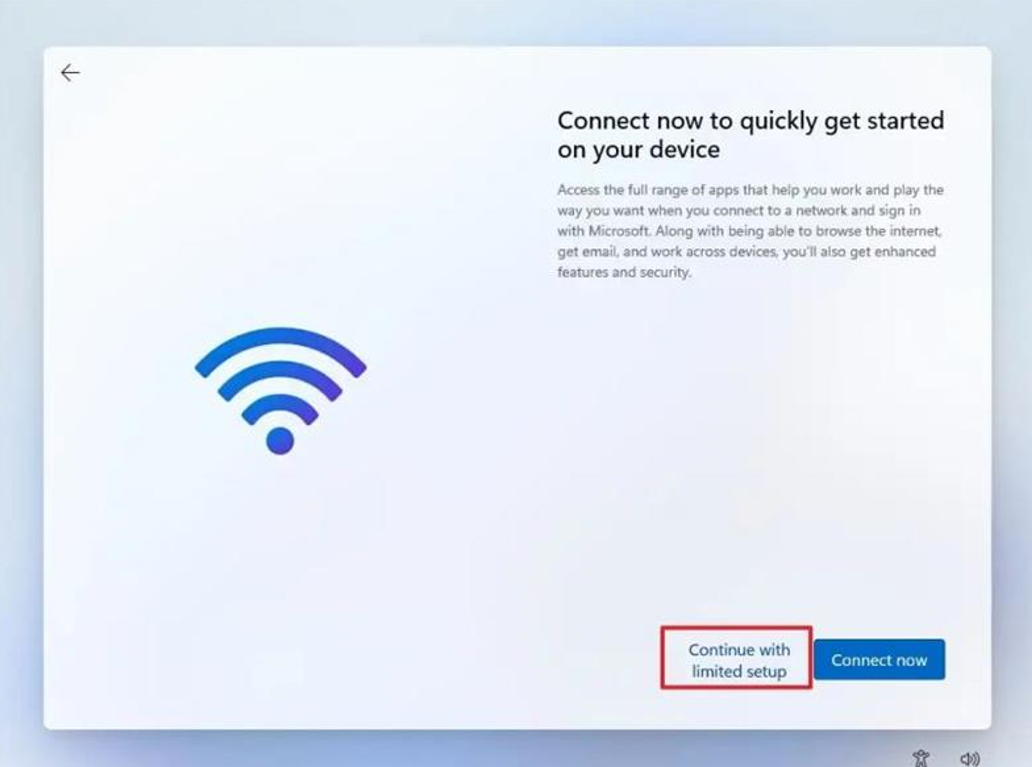
Click the “Continue with limited setup” option.
You have now bypassed the Windows 11 Network Setup menu and create a local user account.

active directory, auditing, compliance, microsoft, networking, shared folder, windows 10, Windows Server
Audit all access to folders and/or files on a server or workstation.
Log onto the server/workstation that you wish to enable auditing on.
Open Local Group Policy Editor.
CTRL + R
gpedit.msc

Browse to the following location: – Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy
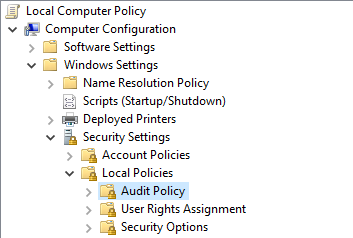
Double click ‘Audit object access’

Select Success and Failure
Click Apply then OK

Exit Local Group Policy Editor
Navigate to the folder/file you wish to track permission changes.
Right click the folder/file then select Properties.
Select the Security tab then select Advanced

Select the Auditing tab then select Continue (if prompted)

Click Add

Click Select a principal

Type ‘everyone’ then select Check Names. – Click OK

Set the Type: to All
Untick the default auditing permissions and only select ‘Change permissions’ – Click OK
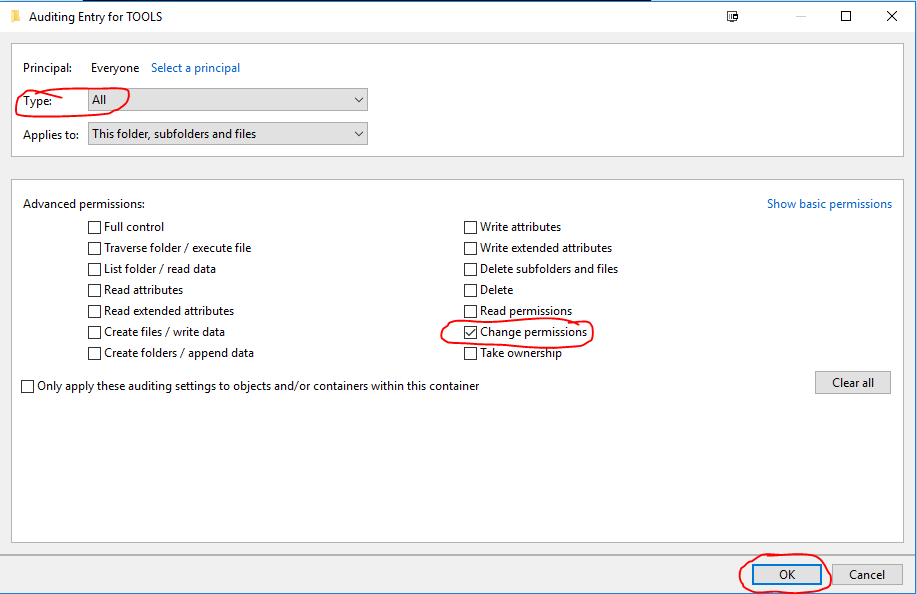
Click OK Twice more.
Open up cmd or powershell as ADMIN
Execute the command: gpupdate /force
Auditing is now implemented on the specific folders/files.
To check audit logs open Event Viewer.
Select the Security Logs
Filter the logs based on Event ID 4670

Exchange, microsoft, networking, Windows Server
Post Windows Updates you may notice Microsoft Exchange services and other dependent services are disabled you can check this by viewing services.msc
Execute the powershell commands below on the Exchange Server to get the services up and running.
First, we have to know which services there are and which need to have their startup type changed. I used the Get-Service cmdlet to find out. In my case, I was just interested in the Exchange Services, so I needed to filter them with the following command:
Get-Service | Where-Object { $_.DisplayName –like “Microsoft Exchange *”} | ft Name,Status
The output told me which services needed to have their startup type changed. To do that, I only had to change the entry after the last Pipe. (To change the startup type I don’t need a displayed output, but I need to change the startup type for the selected services.) This I did with the following cmdlet:
Get-Service | Where-Object { $_.DisplayName –like “Microsoft Exchange *” } | Set-Service –StartupType Automatic
The Exchange Services startup type was changed from disabled to automatic. But they were still not running. To start the services, we can use the following cmdlet:
Get-Service | Where-Object { $_.DisplayName –like “Microsoft Exchange *” } | Start-Service
Next step, IIS
After the Exchange Services have all changed their startup type and status, we are almost done. There is another service we also have to think about IIS
To edit the IIS Admin Service, we can follow the same concept as we did with the Exchange Services. First, we need to identify the services and set the startup type to automatic. For that, we can use this cmdlet:
Get-Service | Where-Object { $_.DisplayName –eq “IIS Admin Service” } | Set-Service –StartupType Automatic
Last but not least, we also need to start IIS Admin Service. This we can do with the following cmdlet:
Get-Service | Where-Object { $_.DisplayName –eq “IIS Admin Service” } | Start-Service

microsoft, networking, openssl, ssl, Windows Server
Convert SSL Certificate to .pfx format (Microsoft IIS)
Obtain a SSL Certficate from a trusted CA (Certificate Authority)
Usually you receive three certificates from the CA, SSL Certificate, CA Bundle and a Private key
In this tutorial we will be using the SSL Certificate and Private key.
Create a new text document on your local machine called private_key.key paste the contents of the private key from the CA into the file.
Save the file. (Make sure it is saved as .key)
Repeat the same process for the SSL Certificate
Copy the contents of the SSL Certificate key field
Create a new text document on your local machine called public_ssl_key.cer paste the contents of the SSL Certificate into the file.
Save the file. (Make sure it is saved as .cer)
You will end up with the following 2 files

To bind the public/private key pair and a set password for .PFX File you will need to download OpenSSL
Download OpenSSL: https://sourceforge.net/projects/openssl/files/latest/download?source=files
Once downloaded extract the contents of the OpenSSL folder and browse to the bin folder.
Open Powershell as Administrator and change to the directory of the bin folder.
Example: cd C:\openssl-1.0.2j-fips-x86_64\OpenSSL\bin
Copy the previously created SSL files containing the Public and Private key into this directory.
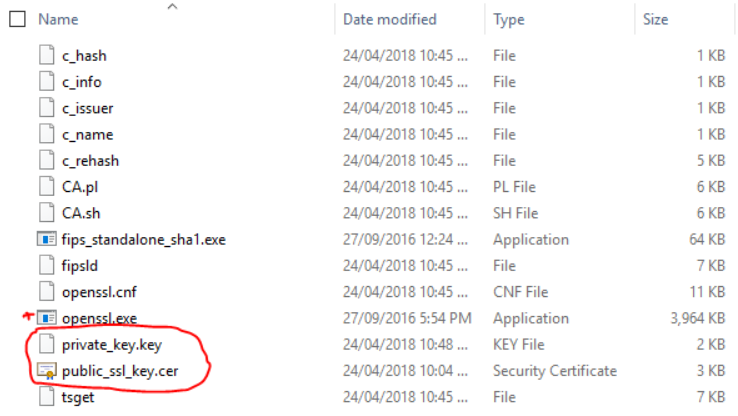
Execute the following command to generate a .PFX file with a password
.\openssl.exe pkcs12 -export -inkey private_key.key -in public_ssl_key.cer -out ssl_cert.pfx
(This will create a .pfx called ssl_cert.pfx and will be saved in same directory as the bin directory.)
You will then be prompted to enter a password for the .PFX file.

The .PFX file will then be generated with a password attached to it.

You can now use this certificate to Import into IIS on Windows Server or via Windows MMC Console.

active directory, microsoft, networking, Windows Server
NOTE: Take a backup and/or snapshot of the VM before making any changes.
When setting up Active Directory, the IT Administrator is given an option to select the folder path to copy the Active Directory database files to. It is advised to always to use a separate partition to save the database files instead of using the default C:\Windows\NTDS\ folder path. This provides an easier opportunity to move the Active Directory database to different location should disk space on the server dry up.
In this Step-By-Step, the lab DC currently stores its AD database files in default C:\Windows\NTDS\ folder. Steps will be detailed amidst this post to move it to a new disk added to the server. The new path it will be moved to will be E:\ADDB
Step 1: Prepping Active Directory to be moved
- Log in to the primary domain controller as domain or enterprise administrator
- In Server Manager, navigate to Tools > Services

- Once mmc loads, right click on Active Directory Domain Services and click stop

4. When asked if it’s okay to stop associated services, click Yes to continue.
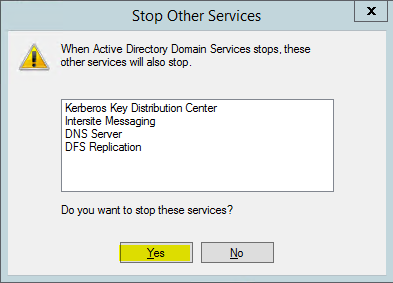
Step 2: Moving the Active Directory database
- Right click on start button and click on Command Prompt (Admin)
2. Once command prompt is visible, type ntdsutil and press enter
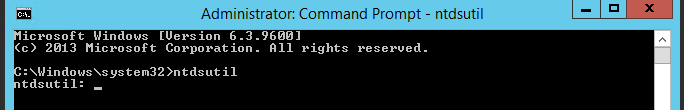
3. Next type activate instance ntds and press enter
4. Then type files and press enter
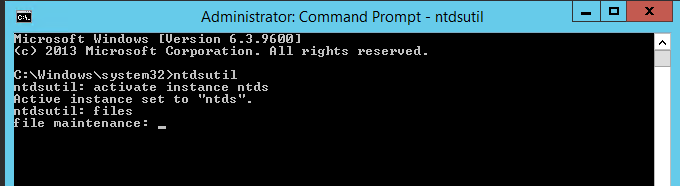
5. In files maintenance the command to move the db is required. As mentioned earlier, the need to move the database to E:\ADDB.Type the following command to enable the move: move db to E:\ADDB
Note: Remember to use quotations (“”) should the path contain a space

6. Once the database files are successfully moved, type the following command to move the logs: move logs to E:\ADDB
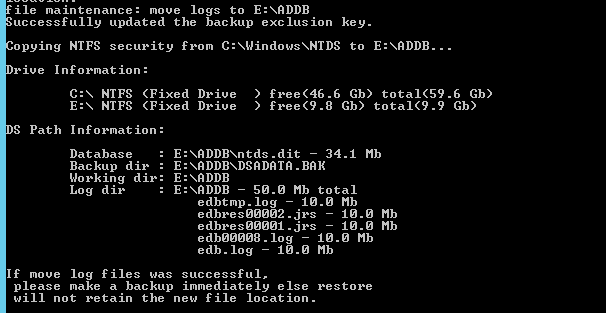
7. Once the move has successfully completed, Return to the initially used services.msc and start Active Directory Domain Services stopped in Step 1
Browse to the new directory where the database files were transferred to confirm they have been transferred successfully.

Restart System.
Test logging in as a AD user.

microsoft, rds, Windows Server
How to modify RDS Idle Timeout and Keep alive time so users don’t get disconnected.
Logon to the RDS server in question.
Open local group policy
Win Key + R > gpedit.msc
Browse to Computer Config > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections (enable keep alive)
Select Enabled for ‘Configure keep-alive connection interval’

Then browse to Computer Config > Admin Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Session Time Limits.
Select the option shown below and enter a time limit that you see fit.

Repeat the same for the User Configuration
Browse to User Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Session Time Limits
Select the option shown below and enter a time limit that you see fit.

Apply gpupdate /force via Powershell or Command Prompt on the RDS Server

Exchange, networking, Windows Server, windows update
Post Windows Updates you may notice MS Exchange services and other dependent services are disabled you can check this by viewing services.msc
Execute the powershell commands below on the Exchange Server to get the services up and running.
First, we have to know which services there are and which need to have their startup type changed. I used the Get-Service cmdlet to find out. In my case, I was just interested in the Exchange Services, so I needed to filter them with the following command:
Get-Service | Where-Object { $_.DisplayName –like “Microsoft Exchange *”} | ft Name,Status
The output told me which services needed to have their startup type changed. To do that, I only had to change the entry after the last Pipe. (To change the startup type I don’t need a displayed output, but I need to change the startup type for the selected services.) This I did with the following cmdlet:
Get-Service | Where-Object { $_.DisplayName –like “Microsoft Exchange *” } | Set-Service –StartupType Automatic
The Exchange Services startup type was changed from disabled to automatic. But they were still not running. To start the services, we can use the following cmdlet:
Get-Service | Where-Object { $_.DisplayName –like “Microsoft Exchange *” } | Start-Service
Next step, IIS
After the Exchange Services have all changed their startup type and status, we are almost done. There is another service we also have to think about – IIS.
To edit the IIS Admin Service, we can follow the same concept as we did with the Exchange Services. First, we need to identify the services and set the startup type to automatic. For that, we can use this cmdlet:
Get-Service | Where-Object { $_.DisplayName –eq “IIS Admin Service” } | Set-Service –StartupType Automatic
Last but not least, we also need to start IIS Admin Service. This we can do with the following cmdlet:
Get-Service | Where-Object { $_.DisplayName –eq “IIS Admin Service” } | Start-Service

networking, windows 10, windows update
ISSUE:
I have a client where the Windows 10 update was installed overnight and it has broken the ability for one of the pc’s to access the other pc for file shares. It is a small network (only 2 pc’s) both running W10 Pro. The main pc can see the shares on the other pc but the one I want to see the main pc shares can only see the main pc in networks but not see any shares.
RESOLUTION:
On the sharing pc, after many attempts in getting it going, I did this and it worked:
- Control Panel > System and Security > Administrative Tools > Local Security Policy > expand Local Policies > Security options
- Click on Network security: Lan Manager Authentication level > Then in the field select > Send NTLMv2 responses only > click on Apply, then ok and close all
- Restart your pc.
NOTE:
Windows 10 version 1709 disables SMB 1.0

networking, windows 10
Ethernet and/or WiFi adapter sees available network,
But will not accept tcp/ip address – Will see Network icon in System Tray but will have “Exclamation mark”.
A reset of winsock and/or IP stack, may resolve the problem.
Usually – have success with a reset of winsock, then a restart.
WARNING !!!
This command must be applied at the local machine level.
Applying command on RDS network stack, will result in loss of connection for all users !!!
1. In the search box on the taskbar, type Command prompt, press and hold (or right-click) Command prompt, and then select Run as administrator > Yes.
Note:- Requires Administrator Credentials
2. At the “Administrative” Command prompt, run the following command.
- Type netsh winsock reset and press Enter.
- Restart computer.
Optional – Full technical Fix:-
At “Administrative” Command prompt, run the following commands in the listed order, and then check to see if that fixes your connection problem:
- Type netsh winsock reset and press Enter.
- Type netsh int ip reset and press Enter.
- Type ipconfig /release and press Enter.
- Type ipconfig /renew and press Enter.
- Type ipconfig /flushdns and press Enter.



































