
active directory, compliance, gpo, group policy, IT Cyber Security Technical Knowledge, microsoft, networking, ransomware, Windows Server
Create Group Policy to Whitelist Applications – Ransomware prevention
Recommended to test Whitelisting in a test environment before deploying in production environment. Purpose is to Block Ransomware, Block Java Updates You will need to manually add Whitelist entries for each new Java Update you wish to install
Go to https://java.com/en/download/
Take note of the latest Java Version (eg, 8u301)
Login to your to a server that can Access/Create/Edit Group Policy objects
Open the run command, type in gpmc.msc – Click OK
Right click on the Organizational Unit you wish add the Whitelist to, Select the first option.
(Create GPO)
Enter a name for the Whitelist, Click OK (i.e CryptoLocker/Ransomware Prevention)
Link the newly create GPO to any other Organizational Units you want to be added to the GPO.
(eg. Right click on Computers OU, ‘select Link an Existing GPO…’ then select the new GPO)
Right click on the GPO, click Edit…
Drill down in; Computer Configuration >> Policies >> Windows Settings >> Security Settings >> Software Restriction Policies
Right click on Software Restriction Policies, Select the first option

Right click on Additional Rules, Select New Path Rule…
Enter the following path: %localAppData%\*\*.exe
Security Level = Disallowed
Click OK

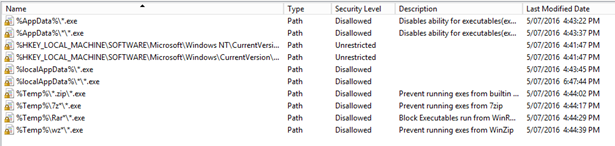
Create Additional Path Rules for the following paths:
%localAppData%\*.exe
%AppData%\*.exe
%AppData%\*\*.exe
%Temp%\*.zip\*.exe
%Temp%\7z*\*.exe
%Temp%\Rar*\*.exe
%Temp%\wz*\*.exe
Your list should look like this:
Exit out of Group Policy Editor.
Create another GPO called Cryptolocker/Ransomware – Whitelist Allow (Link to same OU’s as previous GPO)
Right click on the GPO, click Edit…
Drill down in; – Computer Configuration >> Policies >> Windows Settings >> Security Settings >> Software Restriction Policies
Right click on Software Restriction Policies, Select the first option

Right click on Additional Rules, Select New Path Rule…

Under ‘Path:’ enter the path of the Java Installer you wish to allow:
%localappData%\temp\jre-8u301-windows-i586-iftw.exe
Depending on which version of Java you are updating, replace ‘8u91’ with the version you want to allow.
Set Security Level to ‘Unrestricted’
Enter an appropriate description name.
Click OK.

Verify that new Path Rule has been added to Whitelist.
Close GPO Editor.
Refresh Group policy Management
Go down to the Whitelisting Çryptolocker/Ransomware – Whitelist Allow GPO, click on it once
In the window on the right select ‘Settings’ from the tabs.
Drill down to; Computer Configuration >> Policies >> Windows Settings >> Security Settings >> Software Restriction Policies/Additional Rules
Verify that new Path rule is shown in Policy List.
Exit Group Policy Management.
Go to a machine what is linked to the GPO to test whitelist.
Run Java Updater/Installer
Note the successful installation of Java
If fails = Perform forced Update to GPO
From Administrative Command Prompt,
gpupdate /force

active directory, licensing, microsoft, rds, rwa, Windows Server
You may want to move the existing RDS licenses to a new server to put an old operating system out of production or just upgrade in general.
Login to the server as an administrator
Install the Remote Desktop Licensing Server and Gateway Role via Server Manager
Once installed open Remote Desktop Licensing Manager from Server Manager

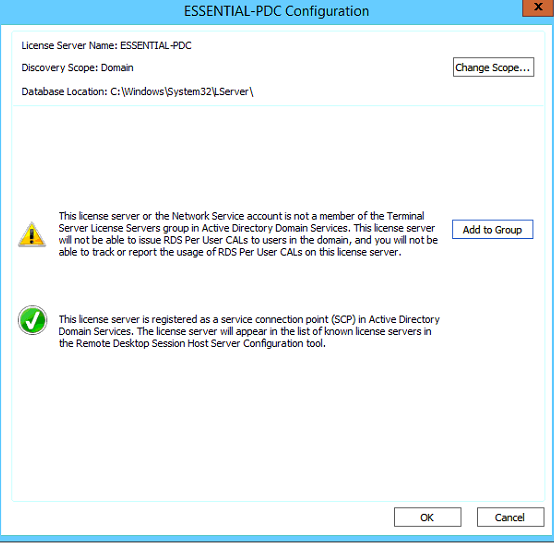
Add the current server into the Terminal Server License Server group as per below,
Select Add to group.


Right click on the server name and select Activate Server

Select Next at the Connect Method screen, (Automatic connection (recommended) is the default)
Enter the relevant information (Company Information) then select Next
Proceed to the next page and fill out additional information.
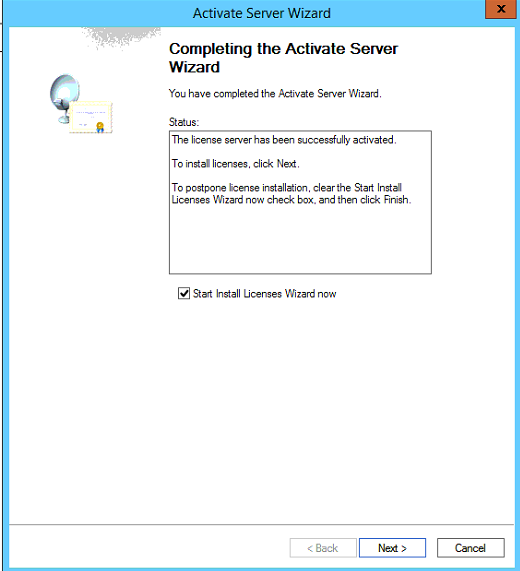
Click Next and the server will activate
On the new licensing server add the old server into the console by select Action > Connect
Enter the IP Address of the old licensing server.
The old server should now be visible on the new server.
To get the licensing ID right click on the old server and select properties
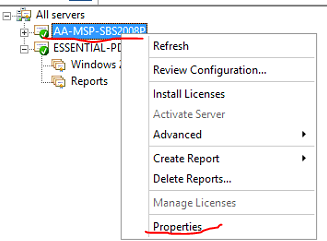
To get the licensing ID right click on the old server and select properties

Select the new licensing server, then go to Action > Manage licenses
Once the window opens select Next
Select the first option as shown below.
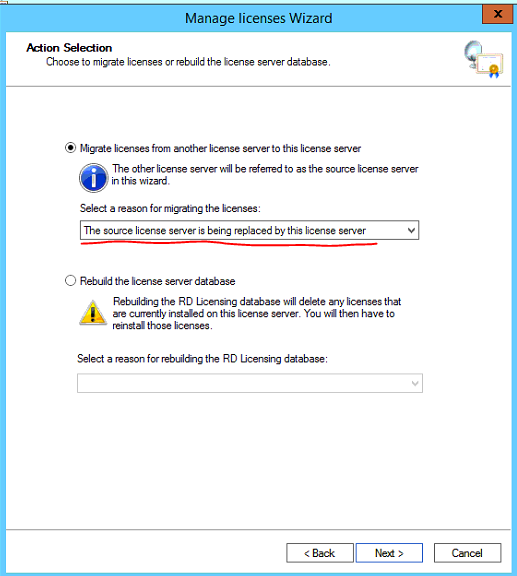
Select the checkbox and select the operation system the old licensing server is running.
Enter the license server ID previously copied, Select Next
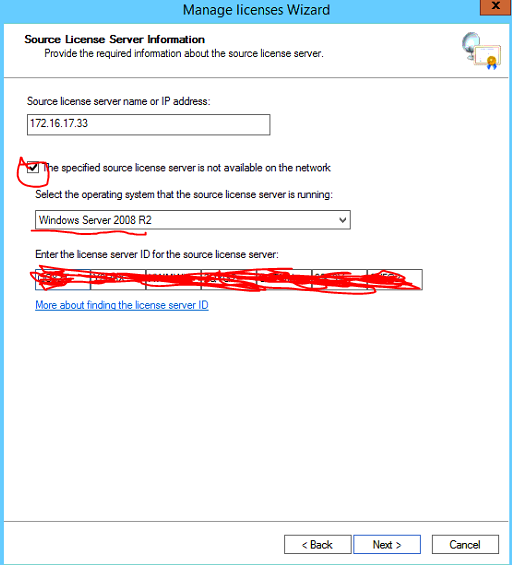
Tick the checkbox to agree to manually remote the licenses from the source server then select next.
If the old licensing Server is running Windows Server 2008 not 2008 R2 you will need the original RDS CAL licenses (Refer to documentation) to apply to the new licensing server as a 2008 server cannot automatically migrate the RDS CAL licenses, only 2008 R2 and above.
If the old licensing Server is running 2008 R2 or above proceed through the wizard to migrate the RDS CAL licenses.
After you have verified the licences are activated and functional you can deactivate the old RDS licensing server.
Once deactivated uninstall the RDS licensing role via Server Manager

microsoft, rds, Windows Server
How to modify RDS Idle Timeout and Keep alive time so users don’t get disconnected.
Logon to the RDS server in question.
Open local group policy
Win Key + R > gpedit.msc
Browse to Computer Config > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections (enable keep alive)
Select Enabled for ‘Configure keep-alive connection interval’

Then browse to Computer Config > Admin Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Session Time Limits.
Select the option shown below and enter a time limit that you see fit.

Repeat the same for the User Configuration
Browse to User Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Session Time Limits
Select the option shown below and enter a time limit that you see fit.

Apply gpupdate /force via Powershell or Command Prompt on the RDS Server

microsoft, rds, Windows Server
In Windows Server 2019 RDS (Not specific to RDS) users default printer may reset from the default printer they previously set each time the server is rebooted.
You will need to edit the local GPO to stop Windows from managing default printers
On the RDS Server open Local GPO Editor
Windows Key + R
gpedit.msc
Browse to User Configuration > Administrative Templates > Control Panel > Printers
Set the setting ‘Turn off Windows default printer management’ to Enabled.
Perform reboot or gpupdate /force of the RDS Server.

If the above group policy does not work it may be due to the way end users connect via their RDP shortcut, If printer redirection is turned on that default printer on their local machine will be selected rather than the default printer for their RDS user profile.
To fix this apply the below group policy setting on the RDS server.
On the Server go into the Local Group Policy Editor:
Windows Key + R
gpedit.msc

In the Local Group Policy Editor navigate to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Printer Redirection.

Enable the Do not allow client printer redirection rule to prevent the server to install “Redirected” printers.

Perform a gpudate /force on the RDS Server or perform a reboot of the RDS Server for the GP setting to be applied.






























